~$: WannaCry Analysis - Malware Analysis
by Annese Gabriele
~$: Executive Summary
- md5:
db349b97c37d22f5ea1d1841e3c89eb4 - sha1:
e889544aff85ffaf8b0d0da705105dee7c97fe26 - sha256:
24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
WannaCry is the most famous crypto-ransomware. WannaCry used the famous Enternal Blue - CVE-2017-0144 Detail vulnerability discovered by National Security Agency (NSA) stolen and made public by Shadows Brokers.
This vulnerability target a bug in the packing handling of SMBv1 protocol. Thaks to this, Wannacry have the worm ability, so is able to propagate itself in the network.
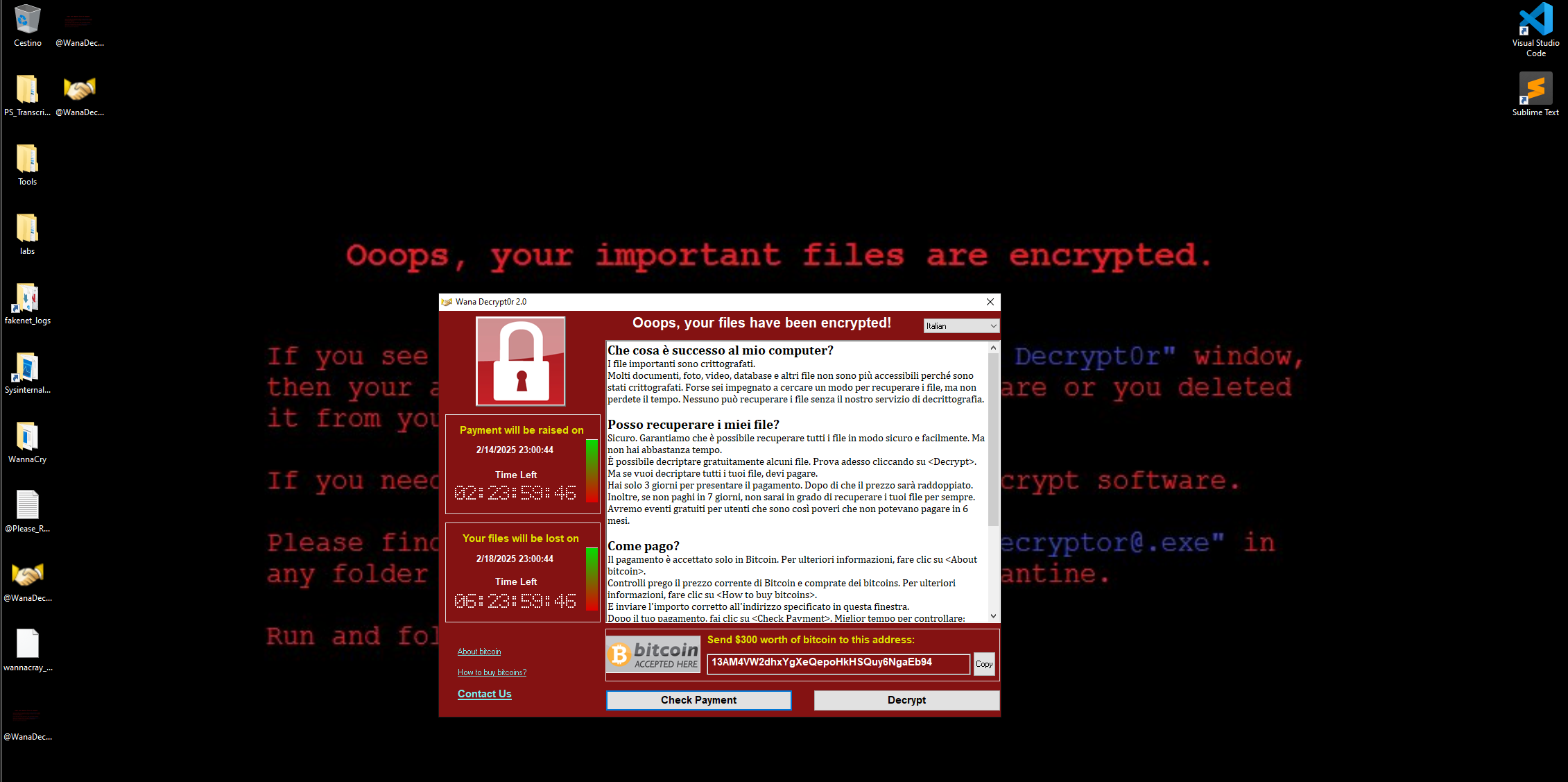
Once the files were encrypted, the threat actors demanded a ransom of $300 worth of Bitcoin. If the ransom is not paid in a specified amount of time, the ransom is increased to $600. This attack infected around 230,000 computers across 150 countries. Marcus Hutchins later discovered a kill switch that stalled the spread of the attack.
~$: High-Level Technical Summary
Wannacry consist in two stages:
-
In the first stage the malware try to contact the
hxxp[://]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]comURL, if the connection is enstablished the program exits, if a connection is established the program proceeds with its execution. Once the program proceeds with execution service is created by the programmssescsv2.0and has display nameMicrosoft Security Center (2.0) Service. During this stage wannaCry will attempt to propagate by reaching out a large range of IPv4 on port 445 to exploit that withEnternal BlueCVE. -
In the second stage the program unpacked the payload form the dropper and proceeds to create a
persistencemechanism such as creating a folder in theC:\ProgramData\<generated_string>\directory and create a file namedtasksche.exeunderC:\Windowscopy itself in to the newly created directory. Once this done a service is created with the name of the generated string for the new path. After a service is created and the payload is executed the encryption process its begin. When the encryption is finished, the GUI of@WanaDecryptor@[.]exewill be displayed where we will be asked to pay a sum in bitcoin to recover the files.
~$: Malware Composition
The Ransomware.WannaCry.exe consist in the following components:
| File Name | What it does | SHA256 |
|---|---|---|
| Ransomware.WannaCry.exe | Dropper with worm ability | 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c |
| tasksche.exe | Dropper/CryptGenRandom | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa |
| taskdl.exe | ??C2 comunicator ?? | 4a468603fdcb7a2eb5770705898cf9ef37aade532a7964642ecd705a74794b79 |
| taskse.exe | ???? | ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa |
| @WanaDecryptor@.exe | Client/Decryptor | 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c |
~$: Static Analysis
~$: Architecture
The malware is written for 32-bit architecture
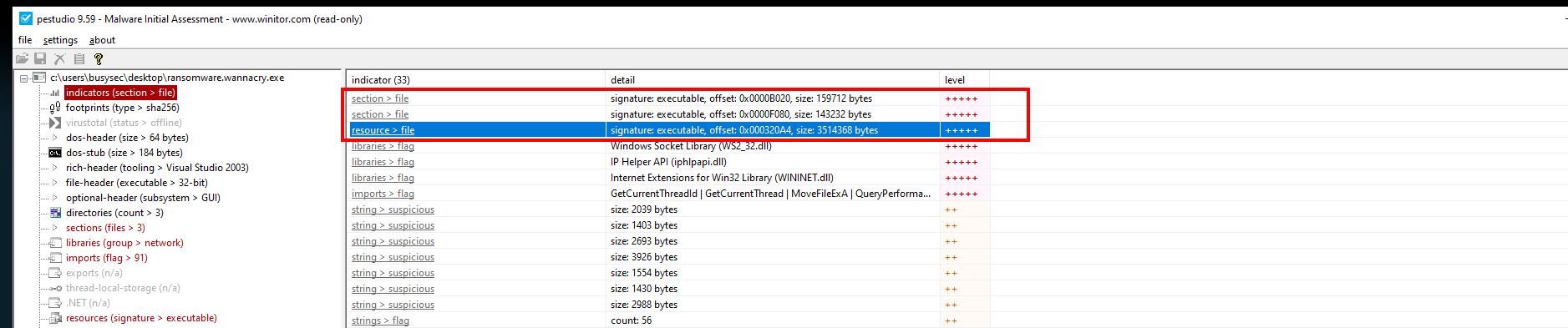
~$:IAT
The import address table (IAT) of WannaCry is:
| DLL Name | Address1 | Address2 | Type | Count | Category | Description |
|---|---|---|---|---|---|---|
| WS2_32.dll | 0x0000A3C4 | 0x0000A144 | implicit | 13 | network | Windows Socket Library |
| iphlpapi.dll | 0x0000A3FC | 0x0000A17C | implicit | 2 | network | IP Helper API |
| WININET.dll | 0x0000A3B4 | 0x0000A134 | implicit | 3 | network | Internet Extensions for Win32 Library |
| KERNEL32.dll | 0x0000A2B0 | 0x0000A030 | implicit | 32 | - | Windows NT BASE API Client |
| ADVAPI32.dll | 0x0000A280 | 0x0000A000 | implicit | 11 | - | Advanced Windows 32 Base API |
| MSVCP60.dll | 0x0000A334 | 0x0000A0B4 | implicit | 2 | - | Windows C Runtime Library |
| MSVCRT.dll | 0x0000A340 | 0x0000A0C0 | implicit | 28 | - | Microsoft C Runtime Library |
The signature: executable, offset: 0x000320A4, size: 3514368 bytes indicated that malware have inside of it another PE files.

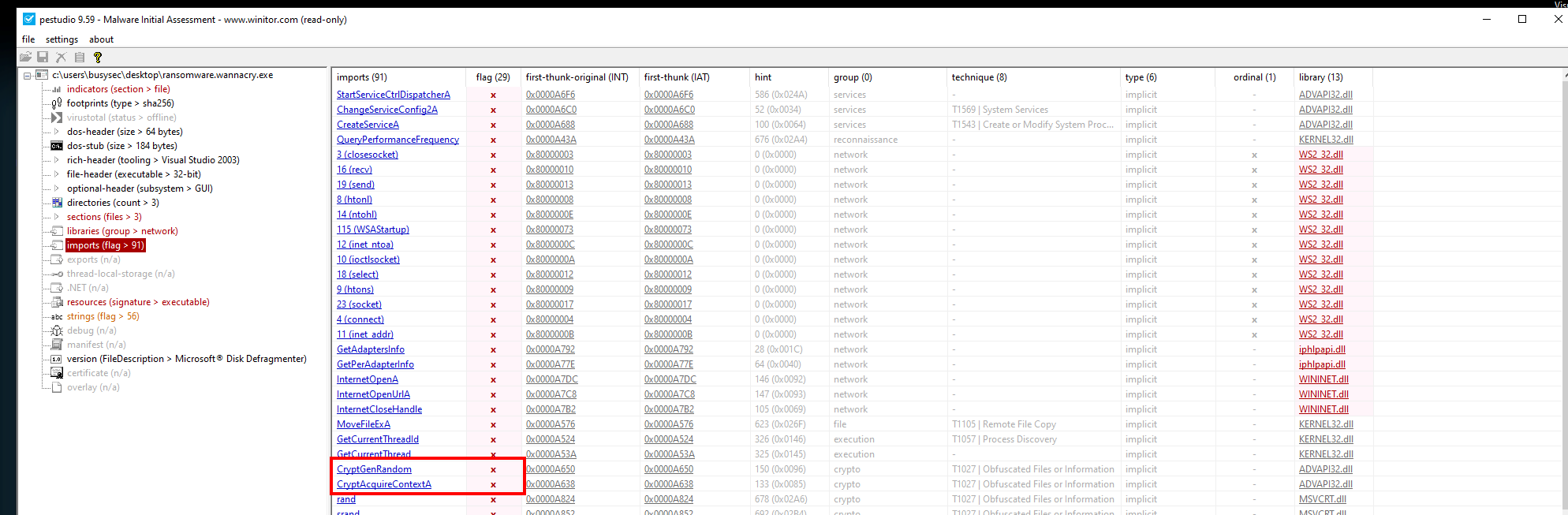
we now that are ransomware infected there are CryptGenRandom CryptAcquireContextA methods of ADVAPI32.dll in the Import Address Table.
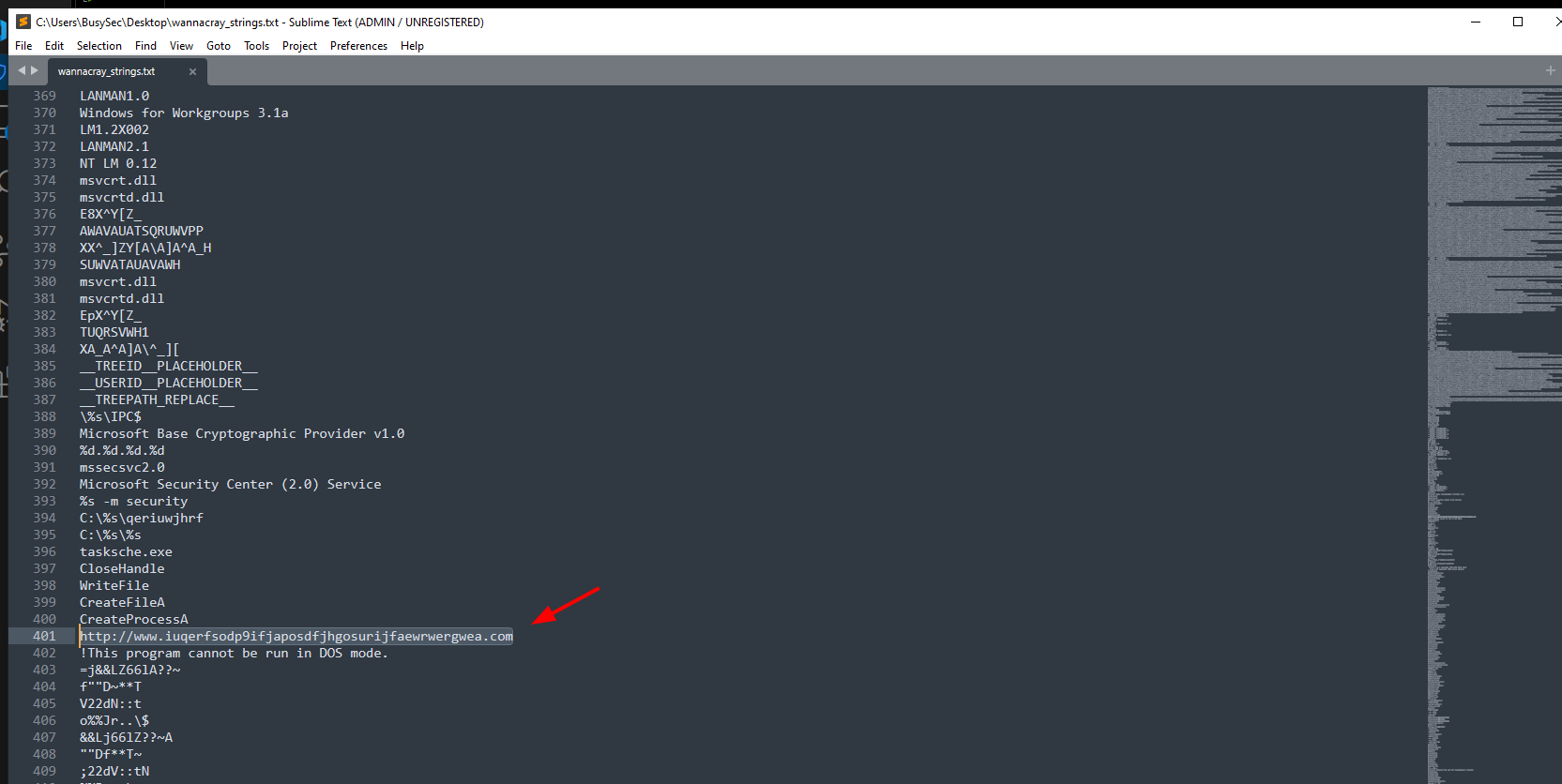
Analyzing the string i founded this path C:\%s\qeriuwjhrf where the %s will be replace by the program when executed.
With PE studio we see the malware have inside another 3 signature of the PE file, this are the possible name of then

I found a strange endpoint. Explore more of that in reverse engineering section.
http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
~$: Reverse Engineering
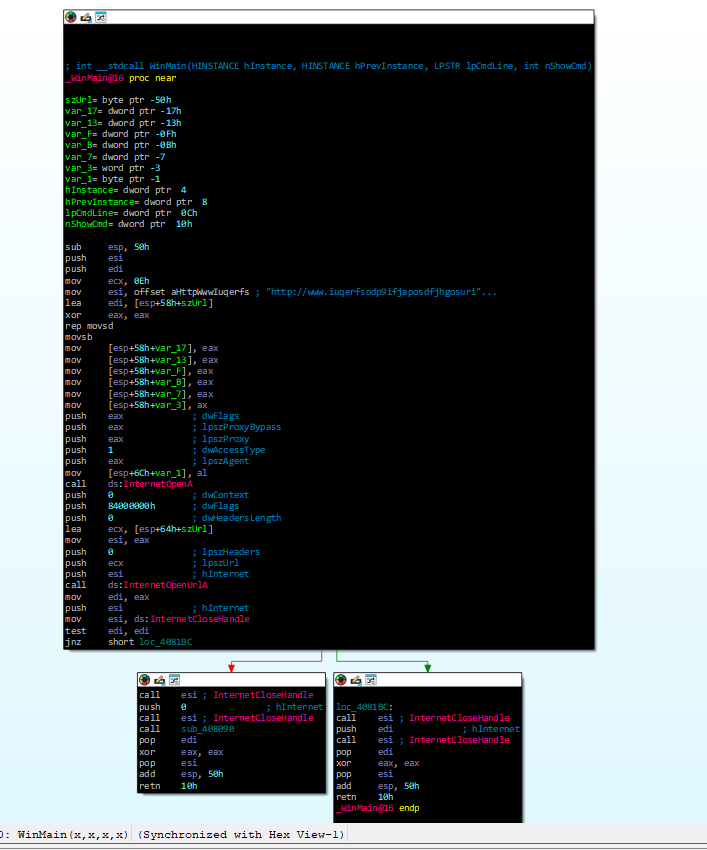
At a start up Wannacry call first the InternetOpenA winApi to initialize WinINet function.
After that the InternetOpenUrlA will invoked this contact trought HTPP the strange endpoint founded during the string analysis http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com, if this endpoint exists the InternetOpenUrlA return a true value.
~$: KillSwitch Mode
The program is be written to close itself the InternetOpenUrlA return a true value. In a nutshell if the http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com endpoint exists Wannacry stop his execution.
WIP…
~$: Dynamic Analysis
~$: Network Indicators
~$: killswitch
In this case i have activated the InetSim on my Remnux machine.
Dns Request
www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
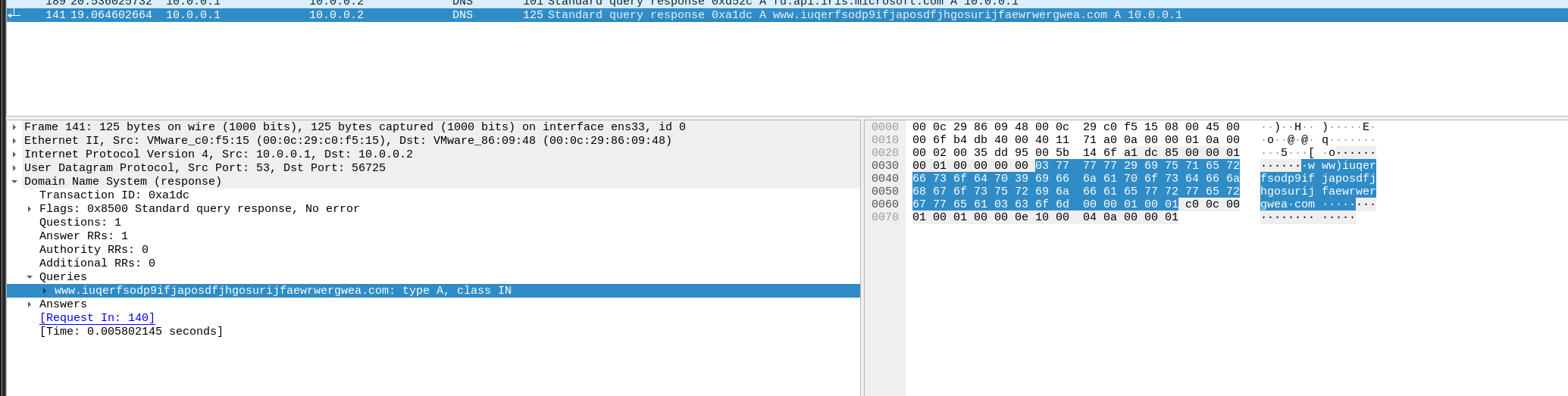
Http Request respond with 200
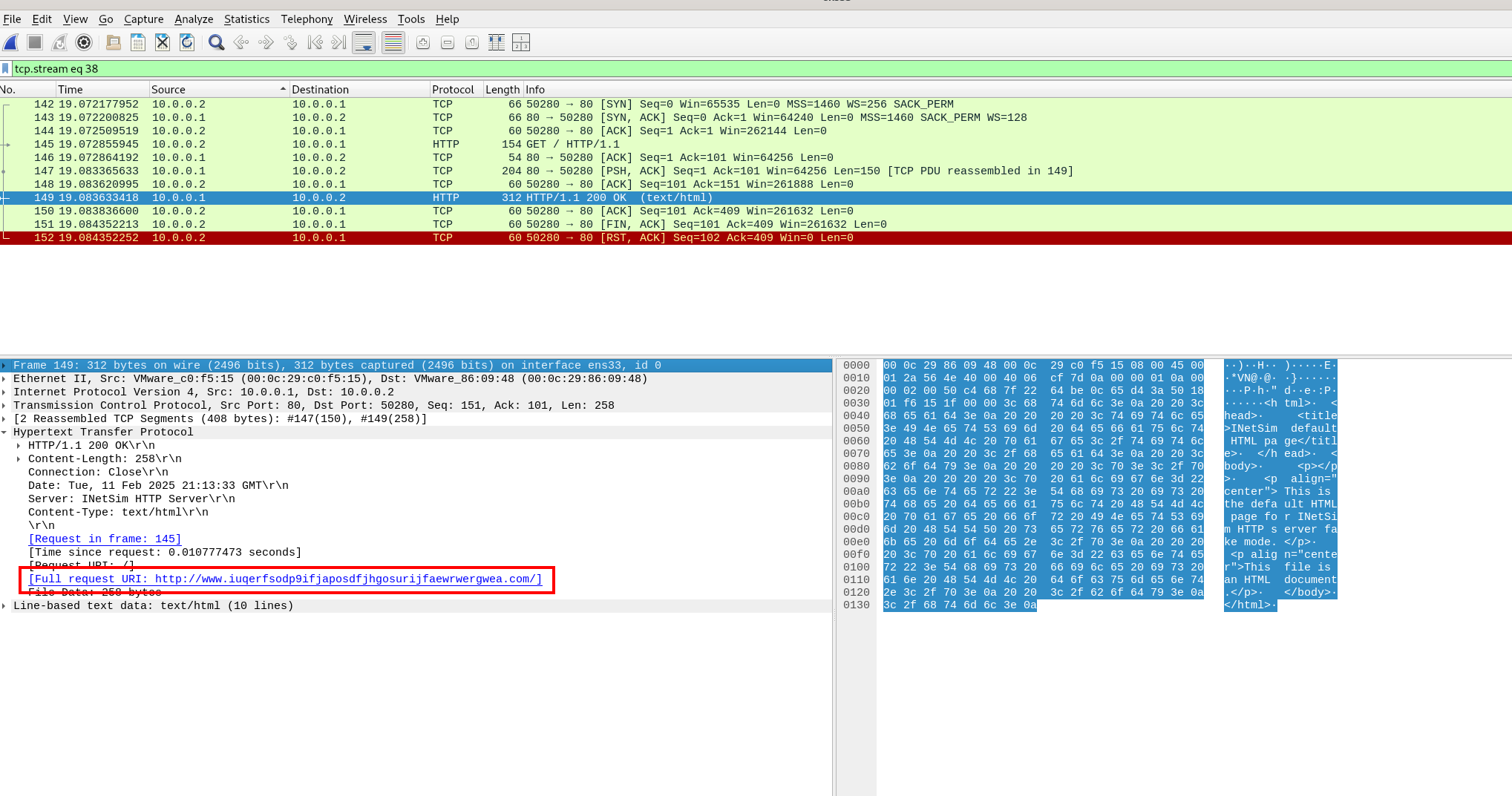
In this case wannaCry doesn’t execute its malicious activities and close itself. Thi is killswitch mechanism founded in the RE section.
~$: Propagation
Wannacry is ransomware but his have the worm ability.
This means its able to propagate itself using the victim network. In this case Wannacry try to propagate itself targeting the 445 port (SMB port).
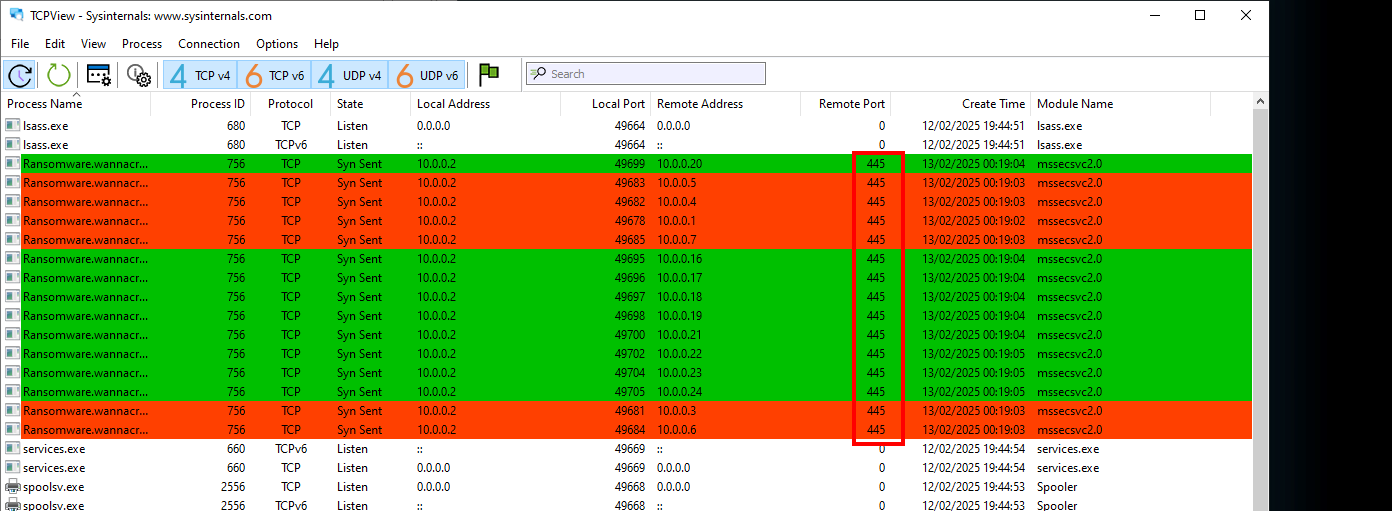
~$: Host base indicator
WannaCry process start second stage payload called tasksche.exe
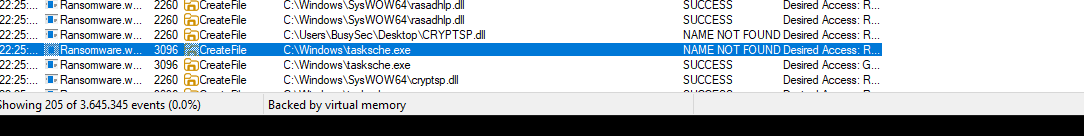
If we go under the process tree view, that program is been executed with /i parameter
C:\WINDOWS\tasksche.exe /i
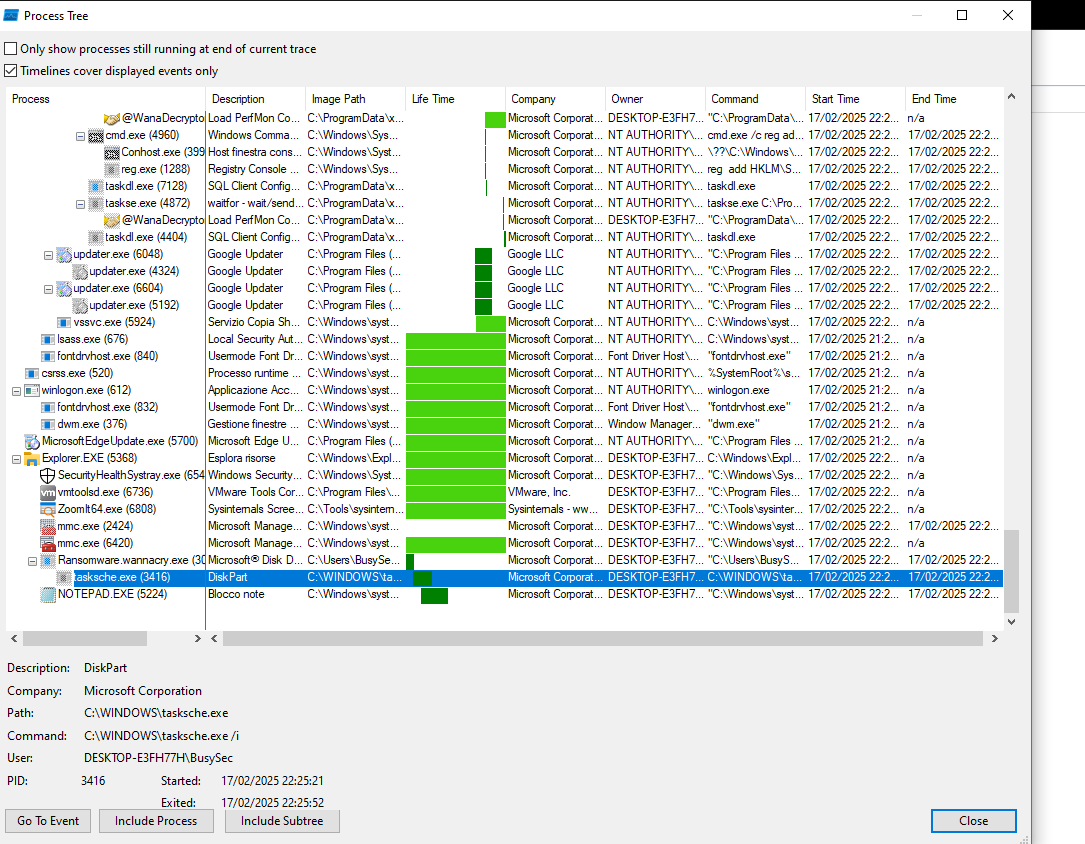
Let’s go back to procomon and filter by ProcessName is taskche.exe.
This second stage create a folder xjskenheabcsyb820. This folder is the staging area of WannaCry.exe malware.
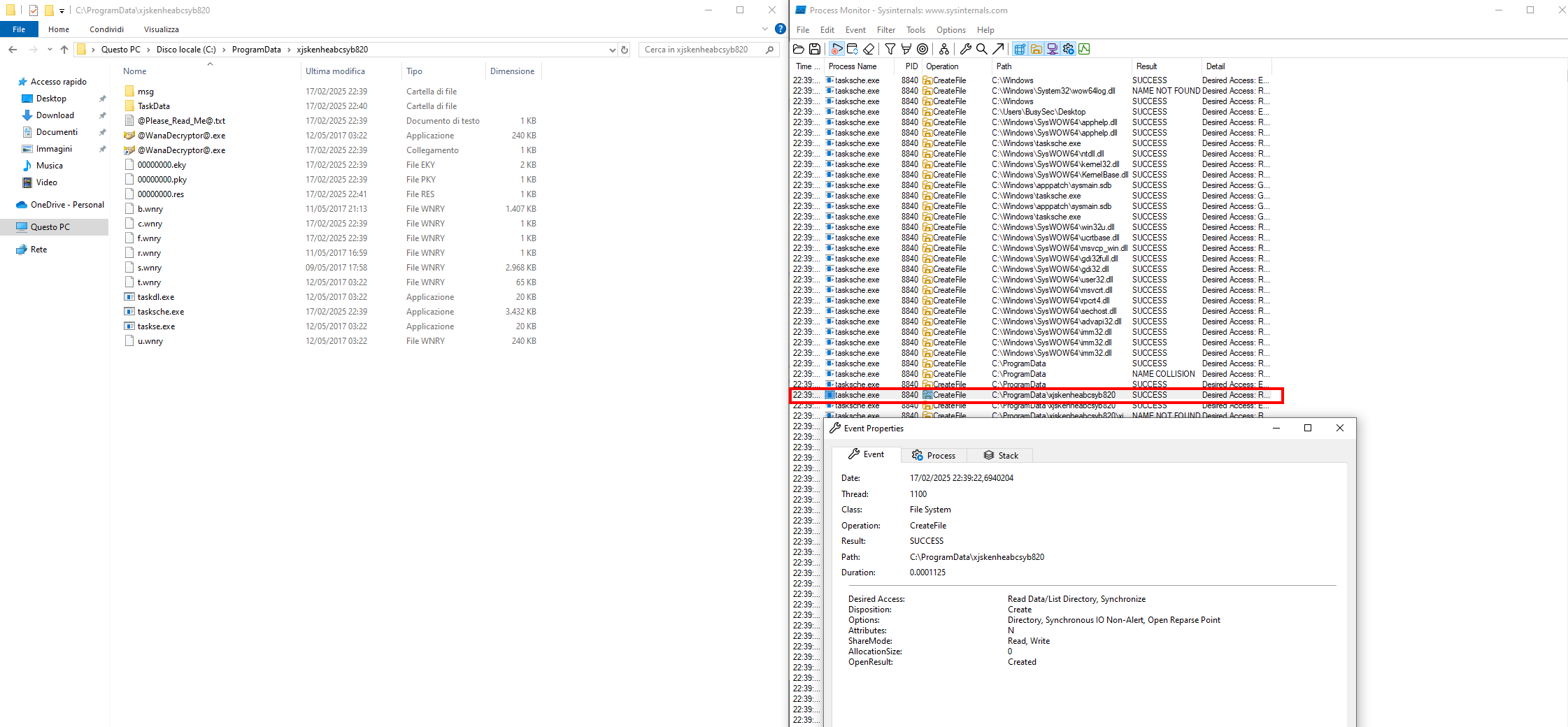
~$: Persistence
Under Windows service i notice there is a new service called xjskenheabcsyb820 like a staging folder.
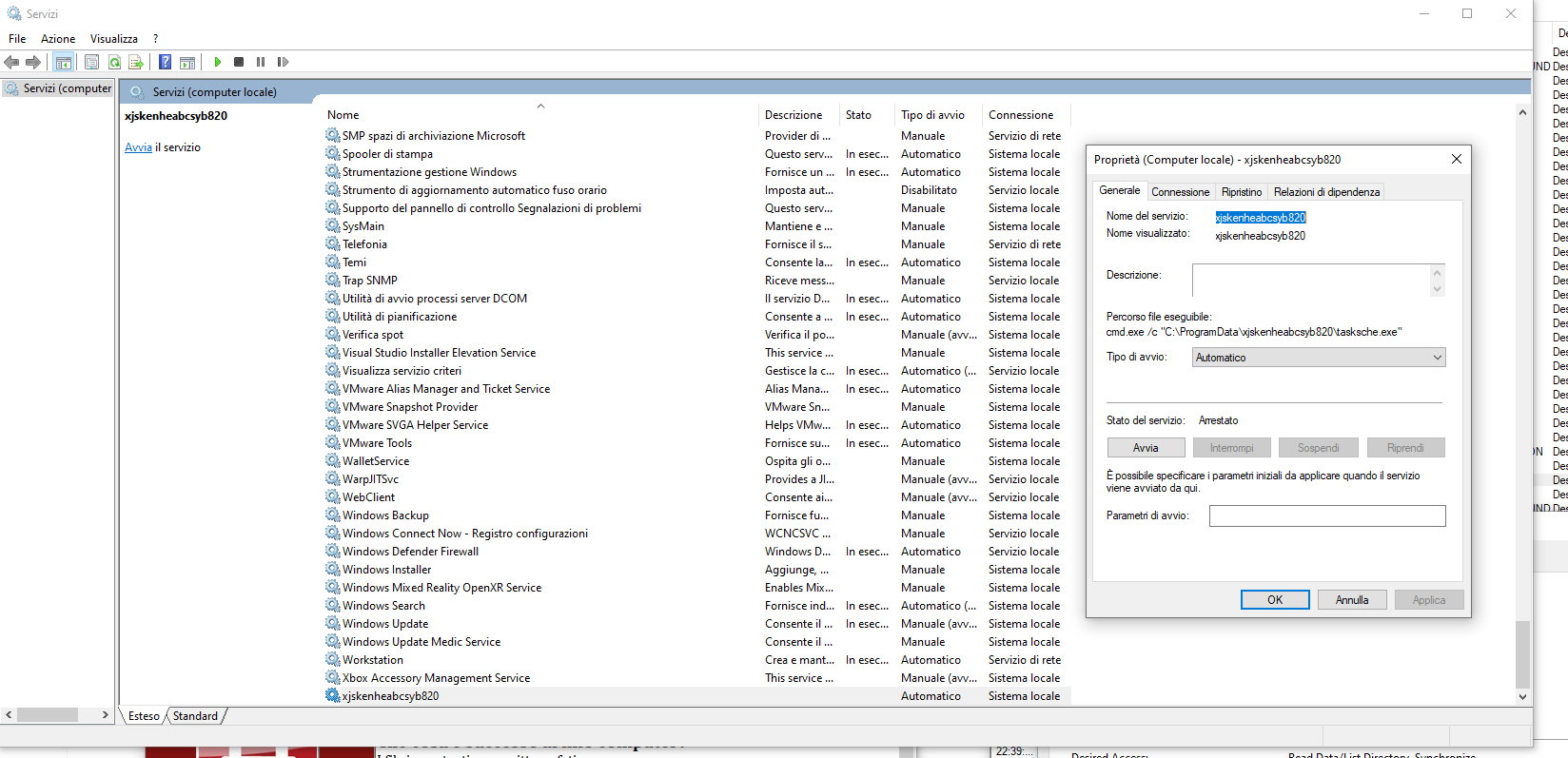
I have insert this filter on Procmon:
- Path contains
SYSTEM\CurrentControlSet\Services\ - Operation is
RegCreateKey
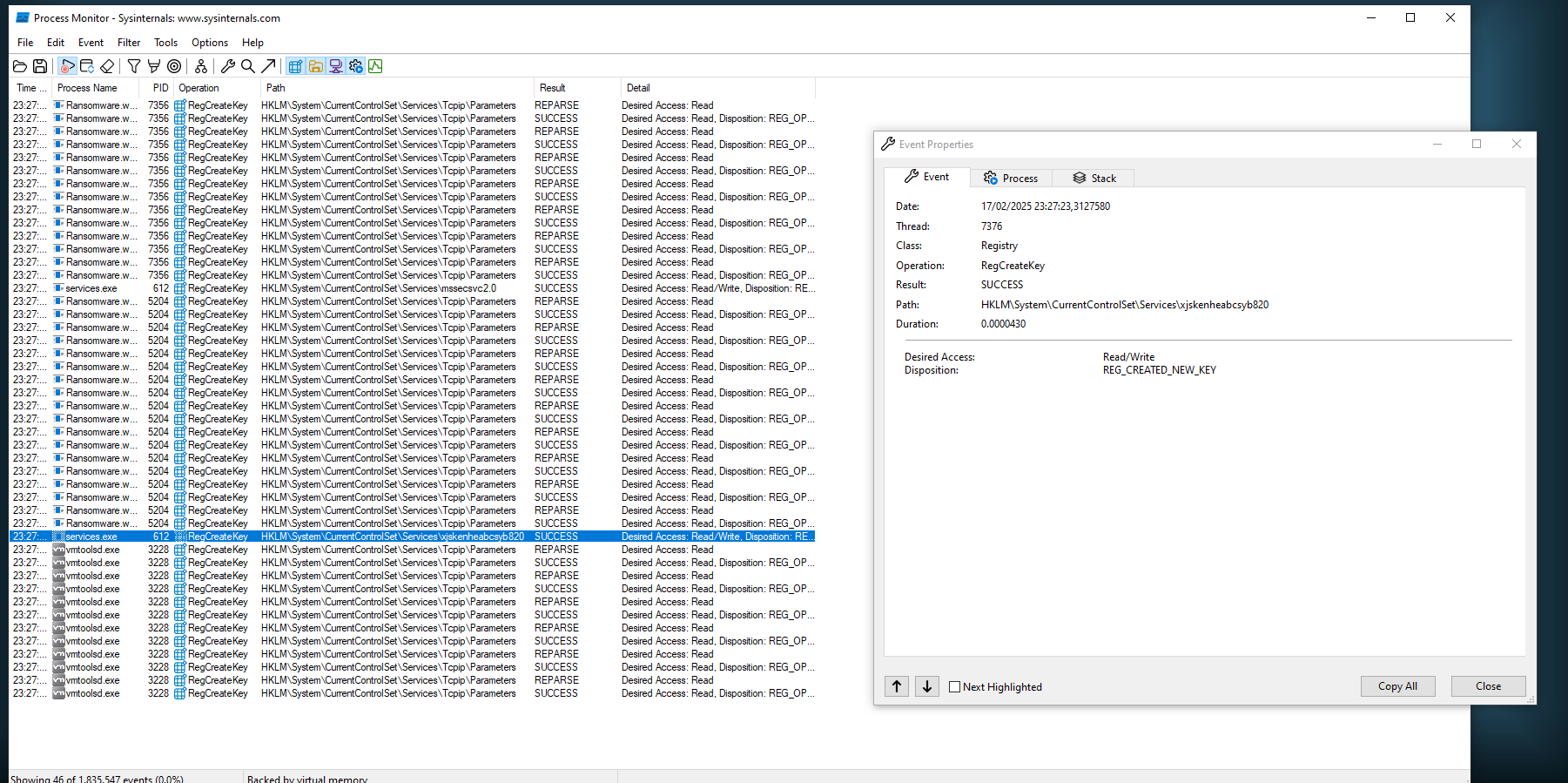
The xjskenheabcsyb820 service execute this commad:
cmd.exe /c "C:\ProgramData\xjskenheabcsyb820\tasksche.exe"
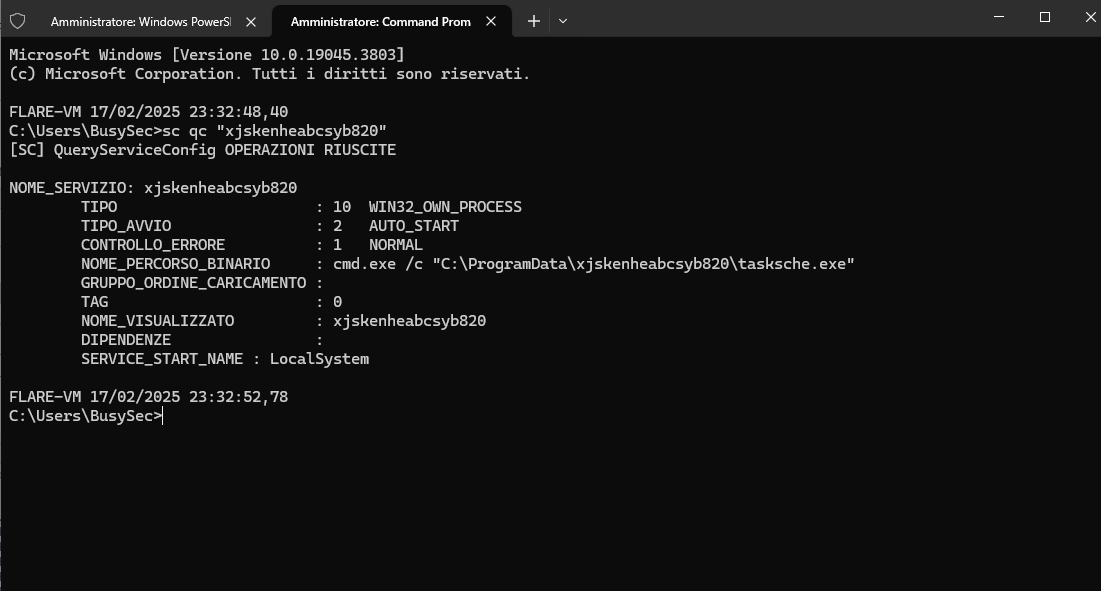
It’s possible verify that with service query:
sc qc "xjskenheabcsyb820"
This is the SHA256 hash of tasksche.exe, maybe in the future i analyze that file more in detail.
| File | HashType | Hash |
|---|---|---|
| tasksche.exe | SHA256 | 2CA2D550E603D74DEDDA03156023135B38DA3630CB014E3D00B1263358C5F00D |
